Commits on Source (84)
-
Marco Picone authored
-
Marco Picone authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
PeterNiblett authored
-
PeterNiblett authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
Marco Picone authored
-
Marco Picone authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
Marco Picone authored
-
Marco Picone authored
-
Ayesha Ayub authored
-
Marco Picone authored
-
Marco Picone authored
-
Marco Picone authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
PeterNiblett authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
Marco Picone authored
-
PeterNiblett authored
-
Ayesha Ayub authored
-
PeterNiblett authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
Ayesha Ayub authored
-
PeterNiblett authored
-
PeterNiblett authored
-
Marco Picone authored
ESTIMED D2.2 Stable Draft Section 4 - Picone See merge request estimed/wp2/gr-mec-dec-050!2
-
Marco Picone authored
# Conflicts: # GR_MEC-DEC_050.md
-
Marco Picone authored
ESTIMED D2.2 Stable-Draft - Clause 5 See merge request estimed/wp2/gr-mec-dec-050!1
-
Marco Picone authored
# Conflicts: # GR_MEC-DEC_050.md
-
Marco Picone authored
Estimed d2.2 stable draft section 6.1 6.2 6.4 ayesha See merge request estimed/wp2/gr-mec-dec-050!3
-
Marco Picone authored
# Conflicts: # GR_MEC-DEC_050.md
-
Marco Picone authored
Estimed d2.2 stable draft section 6.3 niblett See merge request estimed/wp2/gr-mec-dec-050!4
-
Marco Picone authored
-
William Flynn authored
-
Marco Picone authored
-
Marco Picone authored
Deployment options and descriptions See merge request estimed/wp2/gr-mec-dec-050!6
-
Marco Picone authored
-
Marco Picone authored
-
Marco Picone authored
-
Marco Picone authored
-
ankraft authored
-
Marco Picone authored
Some editor marks. Corrected image links. Corrected table layouts See merge request estimed/wp2/gr-mec-dec-050!7
-
Marco Picone authored
-
Marco Picone authored
-
Bob Flynn authored
adding notes for clause 7. brain storming the features needed for stf685 for high level (MEC/oneM2M handover) and low level (select appropriate target MEC/oneM2M).
-
Bob Flynn authored
-
Bob Flynn authored
-
kalebgmichael authored
-
kalebgmichael authored
-
kalebgmichael authored
-
kalebgmichael authored
-
kalebgmichael authored
- Deleted .DS_Store file from the project directory - Updated GR_MEC-DEC_050.md with minor edits (5 insertions, 5 deletions)
-
Bob Flynn authored
Merge branch 'ESTIMED-D2.2-Clause-7-revisions-4.0.3' of https://labs.etsi.org/rep/estimed/wp2/gr-mec-dec-050 into ESTIMED-D2.2-Clause-7-revisions-4.0.3
-
kalebgmichael authored
-
Bob Flynn authored
-
Bob Flynn authored
-
Bob Flynn authored
-
Bob Flynn authored
-
Bob Flynn authored
-
Bob Flynn authored
removed autonumber
-
Bob Flynn authored
-
Ayesha Ayub authored
-
PeterNiblett authored
Replace the figure with a better one
-
kalebgmichael authored
Removed shall statement from clause 7, addressed comments from Bob, added titles for diagrams, introduced the entities description within the text for swarm computing and federated learning
-
kalebgmichael authored
-
Marco Picone authored
Issue #12 - artifacts in Figure 6.3.3-1 See merge request estimed/wp2/gr-mec-dec-050!11
-
Marco Picone authored
# Conflicts: # GR_MEC-DEC_050.md
-
Marco Picone authored
Estimed d2.2 clause 7 revisions 4.0.3 See merge request estimed/wp2/gr-mec-dec-050!10
-
Marco Picone authored
-
Marco Picone authored
-
PeterNiblett authored
-
PeterNiblett authored
-
Ayesha Ayub authored
-
Marco Picone authored
Estimed d2.2 peter niblett issues See merge request estimed/wp2/gr-mec-dec-050!12
-
Marco Picone authored
-
Marco Picone authored
-
Marco Picone authored
Merge branch 'MECDECODE(25)000043_ESTIMED_GR-MEC-DEC-050_stable_draft' into 'R4' MECDECODE(25)000043_ESTIMED_GR-MEC-DEC-050_stable_draft See merge request !5
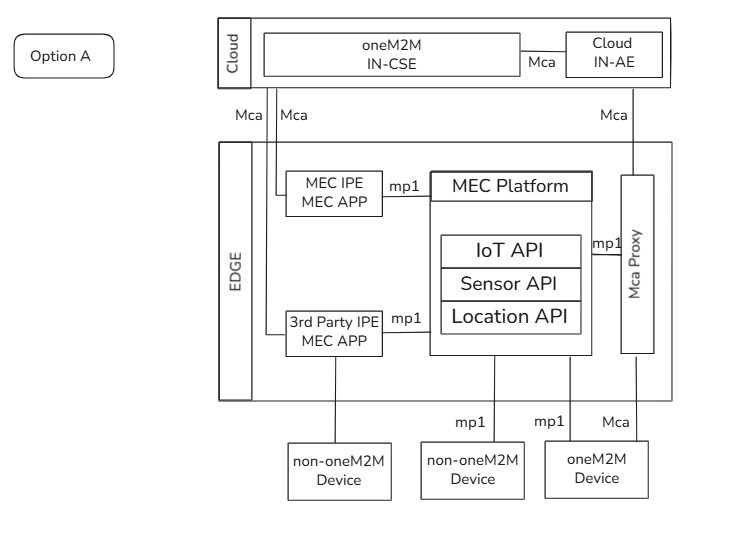
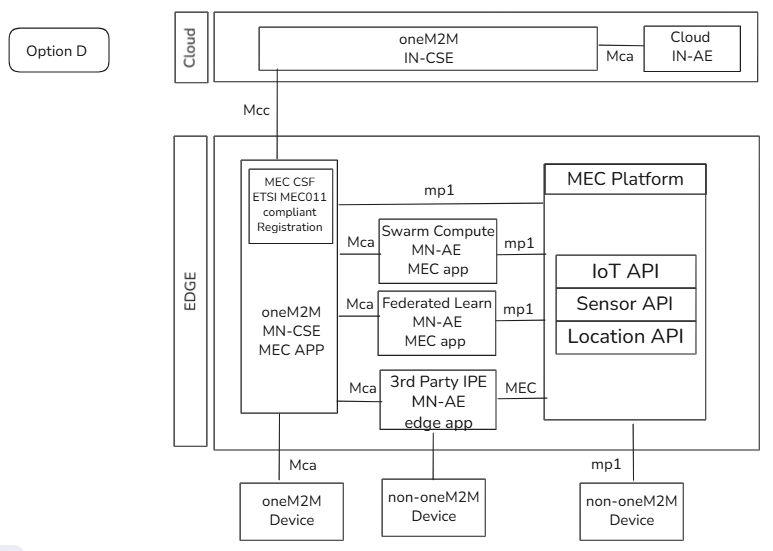
media/OptionA.png
0 → 100644
38.2 KiB
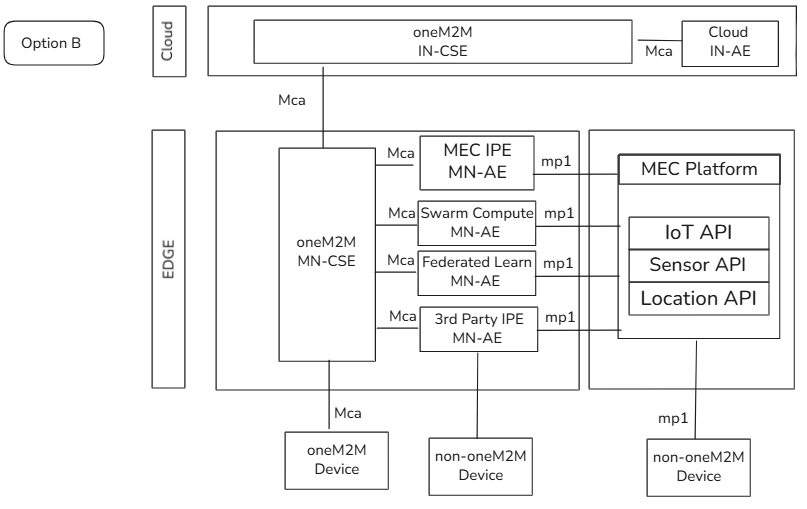
media/OptionB.png
0 → 100644
43.4 KiB
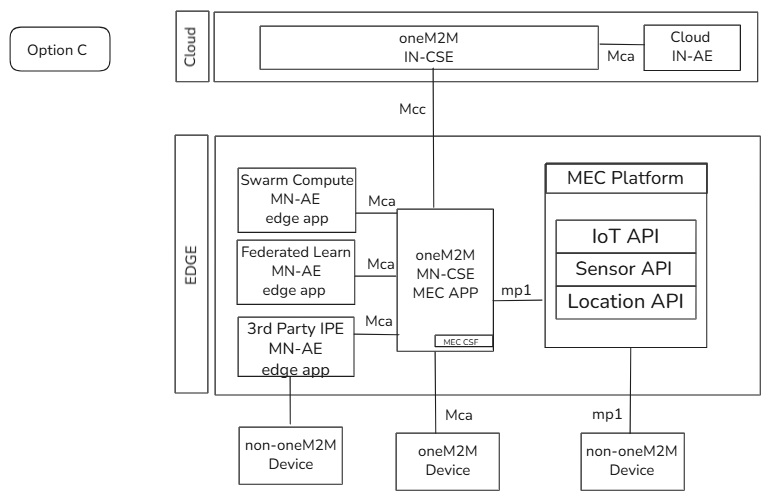
media/OptionC.png
0 → 100644
42 KiB
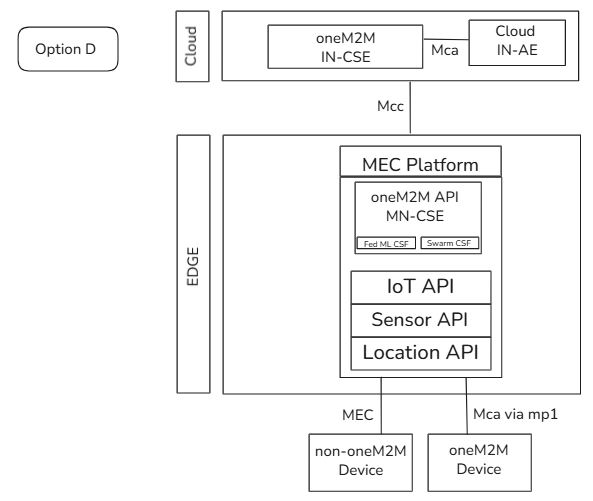
media/OptionD.png
0 → 100644
28.5 KiB
media/OptionD_alt.png
0 → 100644
46.8 KiB
media/deployment_architecture.excalidraw
0 → 100644
This diff is collapsed.
45.1 KiB
68 KiB
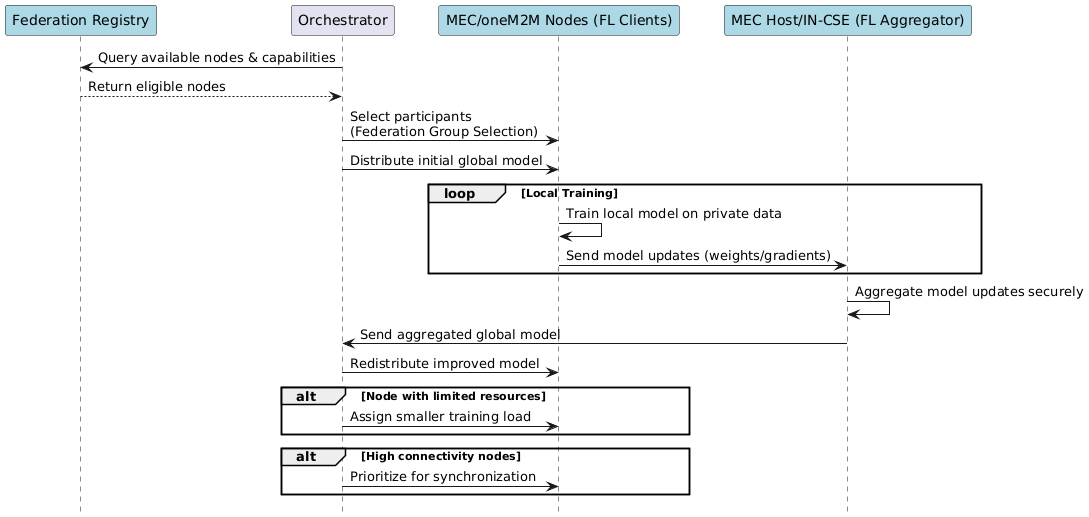
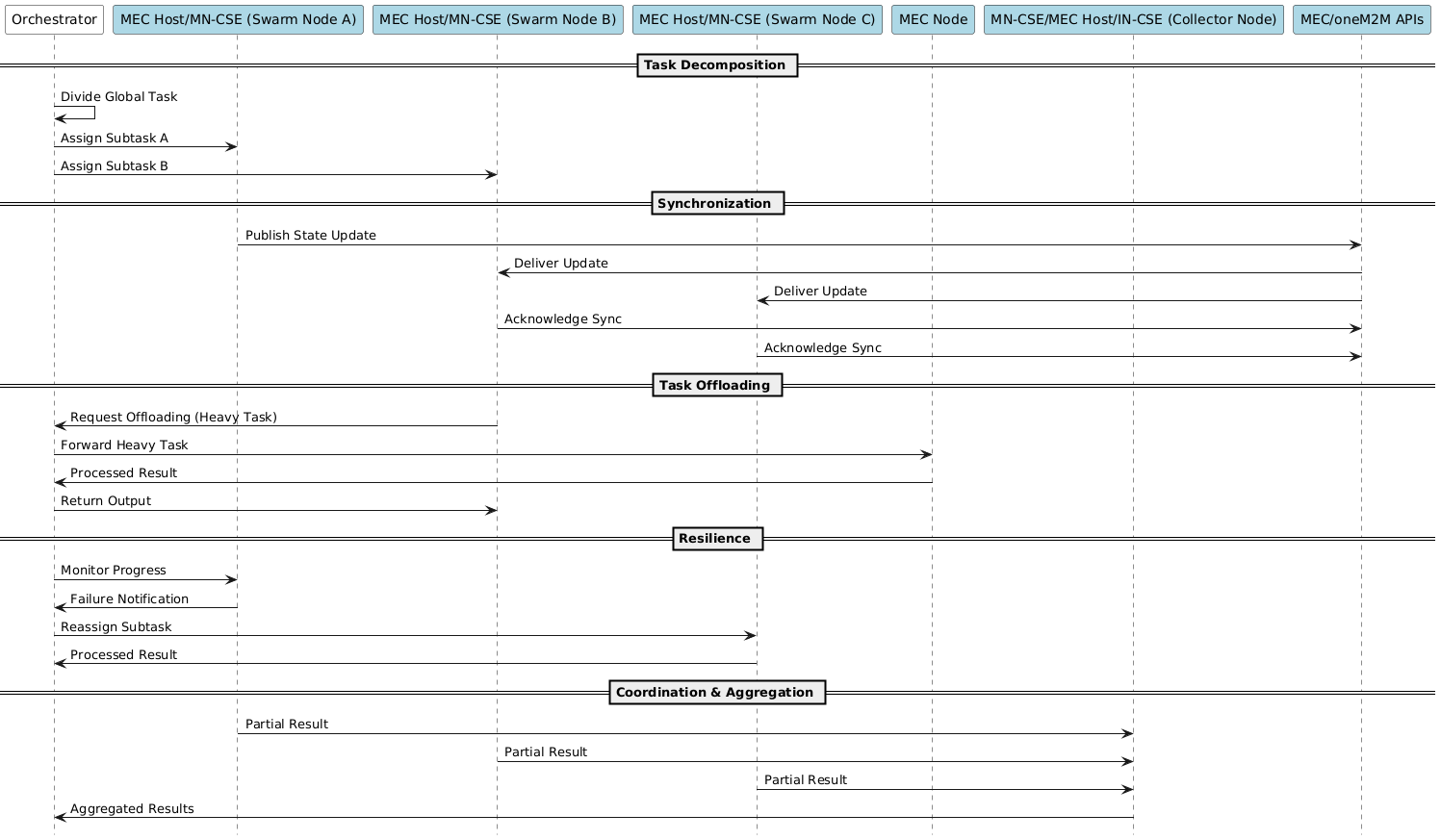
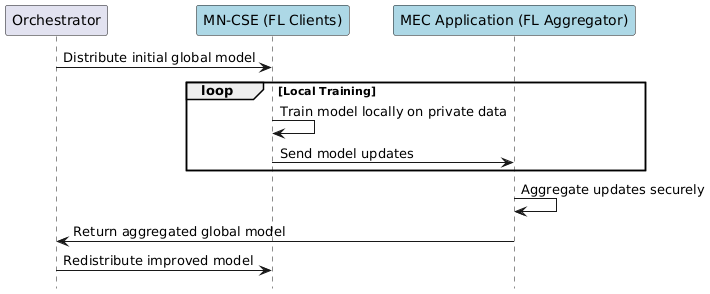
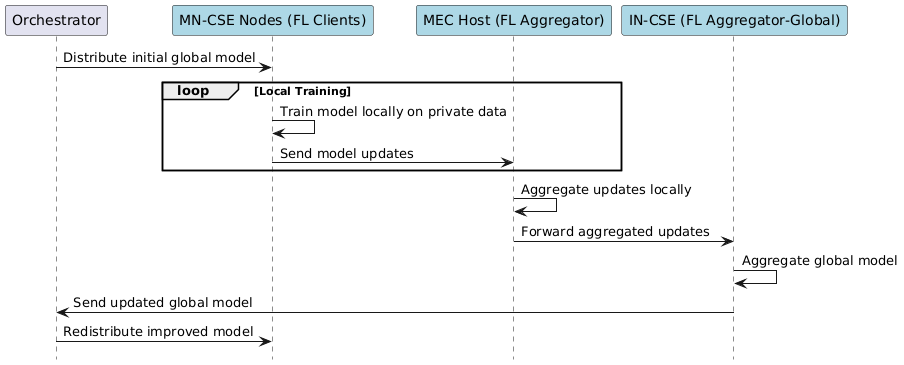
media/federated_learning_option1.png
0 → 100644
22.3 KiB
media/federated_learning_option1.puml
0 → 100644
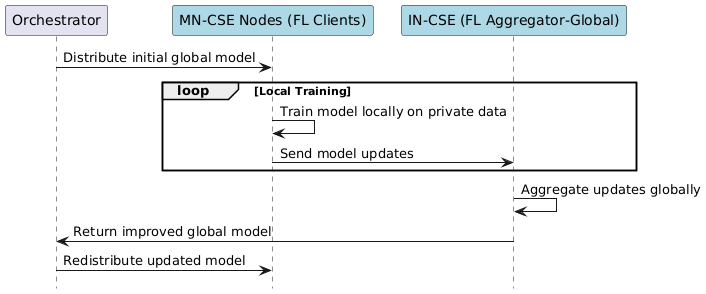
media/federated_learning_option2.png
0 → 100644
28.6 KiB
media/federated_learning_option2.puml
0 → 100644
media/federated_learning_option3.png
0 → 100644
22.3 KiB
media/federated_learning_option3.puml
0 → 100644
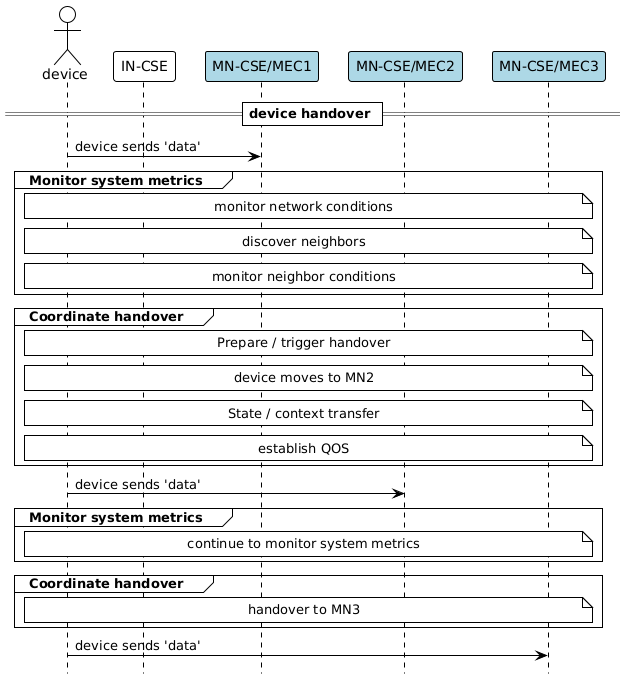
media/handover.png
0 → 100644
41.5 KiB
media/handover.puml
0 → 100644
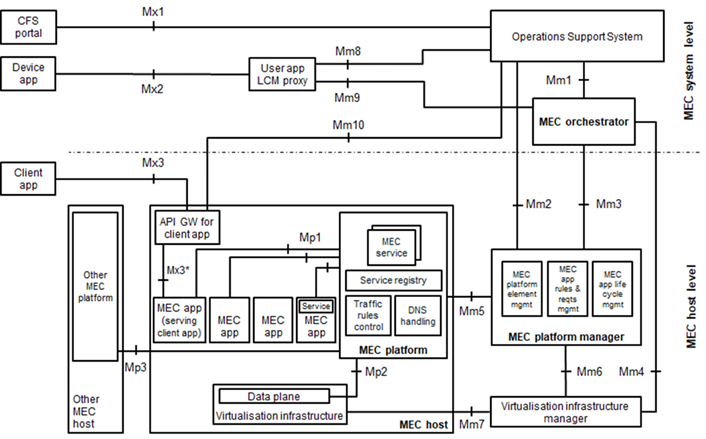
media/mec_arch_6_1.png
0 → 100644
101 KiB